Security , Shop
ITPRO.TV – Mobile Security
In this episode, Ronnie and Don discuss and demonstrate the exposure we have from unmanned mobile devices within a managed network. Don describes some of the problems with them as well as the possible attacks. He then demonstrates the way built security is working to protect itself on an Apple device by segregating applications and isolatingthe communication between application and …
Security , Shop
Pentester Academy – Log File Analysis
A log file analysis helps web masters gather statistics and key figures about the usage of a website or web server. Log file analysis is based on log files, which log all accesses to a web server. Today, JavaScript based tracking tools such as Google analytics have in many cases replaced the traditional analysis of log files.
A log file analysis often involves …
Programming , Security
Coursera.org – Secure Coding Practices Specialization
This Specialization is intended for software developers of any level who are not yet fluent with secure coding and programming techniques.Through four courses, you will cover the principles of secure coding, concepts of threat modeling and cryptography and exploit vulnerabilities in both C/C++ and Java languages, which will prepare you to think like a hacker and protect your organizations information. …
Security , Shop
Pentester Academy – Android Security and Exploitation for Pentesters
Android Security and Exploitation for Pentesters is a course intended for people who want to get started into Android Security, or even who are a bit familiar with the Android security space but want to learn more about Android Application Security. This is a hands-on course where you will get to reverse applications, find security vulnerabilities, perform debugging and API …
Security , Shop
Pentester Academy – USB Forensics and Pentesting
This course will cover USB in detail with an emphasis on understanding USB Mass Storage devices (also known as flash drives or thumb drives).By the end of this course students will know how to sniff USB traffic using open source tools, be able to write-block USB mass storage devices using software and microcontroller-based hardware, be able to impersonate other USB …
Security , Shop
Pentester Academy – Web Application Pentesting
A beginner friendly introduction to Web Application Security with starts from the very basics of the HTTP protocol and then takes on more advanced topics.
A web application penetration test is a type of ethical hacking engagement designed to assess the architecture, design and configuration of web applications. Assessments are conducted to identify cyber security risks that could lead to unauthorised access and/or data …
Security , Shop
Become an AWS Certified Solutions Architect – Associate
This certification path teaches you all you need to get started using Amazon Web Services (AWS), including the AWS Management Console, S3 buckets, EC2 instances, database services, security in the cloud and the costs associated with AWS. The first two courses cover the essentials of AWS. The remaining 16 courses build your knowledge and skills around the five domain areas …
Security , Shop
Become a Certified Information Systems Security Professional (CISSP)
This learning path prepares you to pass the prestigious Certified Information Systems Security Professional (CISSP) exam. As you progress through 24 courses, you’ll build your knowledge across a broad range of technical and management topics ranging from secure software development and cryptography to security governance and risk management. Upon completion you’ll be prepared to earn your CISSP, one of …
Security , Shop
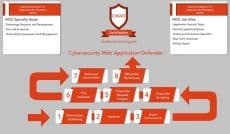
Cybersecurity Web Application Defender
The Cybersecurity Web Application Defender is a knowledge-based certificate offered by CSTT. As part of CCTT certificate program, the certificate is particularly relevant for recent college/university graduates and professionals in IT space, and those looking for a career change to cybersecurity.
What You’ll Learn:
- Understand Threat Modeling
…
Security
Showing 478–486 of 539 results