Security , Shop
Case Studies of Award-Winning XSS Attacks: Part 2
This course is the follow-up to one of my previous courses – “Case-Studies of Award-Winning XSS Attacks: Part 1”. We will continue our XSS hunting journey and you will learn more about award-winning XSS attacks.
There are many people hunting for XSSs, but only a few of them are successful and earn a 4-digit ($$$$) reward per single XSS. What makes …
Security , Shop
Certified Incident Handler (ECIH) v2
This course covers the exam objectives of EC-Council’s Certified Incident Handler v2 (E|CIH) program. It discusses the basic skills to handle and respond to security events and addresses various underlying principles and techniques for detecting and responding to current and emerging computer security threats. The incident handling skills taught in E|CIH are complementary to the job roles below as well …
Security , Shop
Deep Dive into Wireless Security
This course is ideal for penetration testers, security enthusiasts and network administrators. It will take you on a unique journey starting from learning the core concepts of Wi-Fi technology to performing systematic penetration testing against Wi-Fi networks. Additionally, the course will help you grasp and apply the necessary skills and tools that you will need to hack Software Defined Radio. …
Security , Shop
Red Team Ops
Red Team Ops is an online course that teaches the basic principals, tools and techniques, that are synonymous with red teaming.
Students will first cover the core concepts of adversary simulation, command & control, and how to plan an engagement. They will then learn about each stage of the attack lifecycle from initial compromise, to full domain takeover, data hunting, …
Security , Shop
Cracking Software Practicals (CSP)
Real software are commercial proprietary software. We are doing this for educational purposes and not to harm software developers. This skill and knowledge benefits developers in that they are better able to secure their software. The concept is similar to ethical hacking – the only way to defend against hackers is to know how hackers break in. Similarly, for software …
Security , Shop
Windows Red Team Lab
This is a companion course for our Windows Red Team Lab. It does however touch upon interesting concepts you can learn when doing pentests on a Windows Active Directory environment.
HOMEPAGE – https://www.pentesteracademy.com/course?id=44
Our Price: $3
Security , Shop
Learn Cloud Security Architecture
The Cloud Security Architecture skill path teaches you enterprise security architecture concepts related to the cloud, including cloud infrastructure, data and application security.
This learning path provides an in-depth look at cloud security architecture. As you progress through 17 courses, you’ll build your knowledge and skills around cloud infrastructure and design, cloud data and application security, network security, secure storage, cryptography, …
Security , Shop
OWASP Top 10 Security Fundamentals
This course follows a hands-on approach: you’ll exploit at least ten vulnerabilities in a deliberately vulnerable web application. In each session, we will review and briefly discuss a single OWASP Top 10 risk and then you’ll be guided to search and exploit that weakness in the target application. Since you’ll have access to the web application source code, you’ll be …
Security , Shop
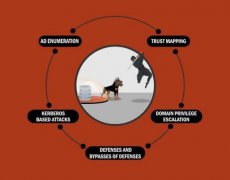
Attacking and Defending Active Directory BootCamp
This is a 4-week beginner-friendly bootcamp, designed to teach security professionals how to identify and analyze threats in a modern Active Directory environment. The bootcamp will cover topics like Active Directory (AD) enumeration, trust mapping, domain privilege escalation, Kerberos based attacks, SQL server trusts, defenses and bypasses of defenses.
The bootcamp will teach you how to attack and defend Enterprise Active …
Hacking
Showing 64–72 of 193 results