Security , Shop
Introduction to OWASP Top 10 Security Risks
This course will introduce students to the OWASP organization and their list of the top 10 web application security risks. The course will analyze these risks from the attacker’s perspective and provide defensive techniques to protect against these risks.
HOMEPAGE – https://www.anonymz.com/?https://acloudguru.com/course/introduction-to-owasp-top-10-security-risks
Our Price: $2.99
Programming , Security
Python 201 for Hackers
The Python 201 for Hackers course builds upon the Python 101 for Hackers course by moving beyond the basics. You will learn more advanced programming concepts and techniques, with a focus on how to use and apply Python as a Windows hacking tool.
Prior Python programming knowledge is required to be successful in this course. The Python 201 for Hackers course content …
Programming , Security
DevSecOps: Beginner Edition Bootcamp
Get a hands-on introduction to DevSecOps basics with a focus on implementing Devops and DevSecOps pipelines in on-premise, hybrid and on-public cloud models.
HOMEPAGE – https://www.anonymz.com/?https://bootcamps.pentesteracademy.com/course/devsecops-on-demand
Our Price: $6.99
Security , Shop
The Complete Cyber Security Course! – Volumes 1, 2, 3 & 4
YOU CAN BECOME A CYBER SECURITY EXPERT!
There is no need to spend years going through hundreds of different courses and still being average when it comes to practical knowledge of cyber security.
Imagine you know everything important in the domain of cyber security…
You can tackle all types of online threats, including advanced hackers, trackers, exploit kits, mass …
Security , Shop
A Complete Practical Approach To Malware Analysis And Memory Forensics
Malware analysis and memory forensics are powerful analysis and investigative techniques used in reverse engineering, digital forensics, and incident response. With adversaries getting sophisticated and carrying out advanced malware attacks on critical infrastructures, Data Centers, private and public organizations, it is essential for cyber-security professionals to have the necessary skills to detect, respond and investigate such intrusions. Malware analysis and …
Security , Shop
The RedTeam Blueprint – A Unique Guide To Ethical Hacking
Welcome to the FIRST complete guide to Ethical Hacking! A lot of other Ethical Hacking or Security courses will just teach you how to hack or attack target systems. Learning just this aspect of Ethical Hacking WILL NOT GET YOU THE JOB IN THE REAL WORLD! The RedTeam Blueprint was designed and developed by Silicon Valley Hackers to actually land you the hacking job or penetration testing!
The reason the course was designed in this unique way …
Security , Shop
Android & Mobile App Pentesting
In this course you will be shown how to perform professional penetration testing activities against Android and iOS mobile applications, by means of reverse engineering, static analysis and dynamic analysis. First you will learn all about the attack surface of Android applications and the techniques to exploit each covered vulnerability (incl. reverse engineering). Specifically, Android OS fundamentals (Android VM, Android …
Security , Shop
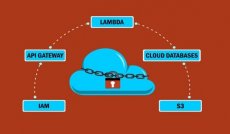
Cloud Security: AWS Edition
Most AWS deployments are breached by a common set of vulnerabilities which attackers repeatedly use.
In 5 weeks, this bootcamp teaches you to identify, exploit and secure vulnerabilities in the 5 most commonly used AWS components, so you can be a job-ready Cloud Security practitioner.HOMEPAGE – https://www.anonymz.com/?https://bootcamps.pentesteracademy.com/course/cloud-security-aws-jun-21
Our Price: $6.99
Security , Shop
HackerOps – Antisyphon Training
To conduct an advanced attack, you need more than just a collection of simple scripts. In addition to talent, you need a large amount of managed and unmanaged code. The more code and resources that are required to conduct an engagement, the more time we need. Time is something we don’t have a lot of on an engagement.
Today, to be …
Security
Showing 415–423 of 578 results