Security , Shop
Cyber Threat Hunting
This learning path teaches you the necessary skills to becoming a successful threat hunter. As you progress through eight courses, you’ll build core hunting skills such as intelligence gathering, investigation techniques and remediation methods. Upon completion, you’ll have the knowledge and skills to carry out cyber threat hunting activities with an organization that will ultimately deliver proactive defenses against possible …
Programming , Security
Secure Programming with C
Secure coding with C is a top concern. Although the C programming language, which is commonly used in numerous applications and operating systems is popular, flexible, and versatile, it is inherently vulnerable to exploitation.
Writing a secure code is crucial. Because there is no direct method to handle the exception (no inbuilt try and catch such as in another high-level language …
Security , Shop
OWASP Top 10 Security Fundamentals
This course follows a hands-on approach: you’ll exploit at least ten vulnerabilities in a deliberately vulnerable web application. In each session, we will review and briefly discuss a single OWASP Top 10 risk and then you’ll be guided to search and exploit that weakness in the target application. Since you’ll have access to the web application source code, you’ll be …
Security , Shop
Attacking and Defending Active Directory BootCamp
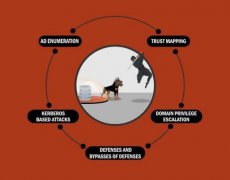
This is a 4-week beginner-friendly bootcamp, designed to teach security professionals how to identify and analyze threats in a modern Active Directory environment. The bootcamp will cover topics like Active Directory (AD) enumeration, trust mapping, domain privilege escalation, Kerberos based attacks, SQL server trusts, defenses and bypasses of defenses.
The bootcamp will teach you how to attack and defend Enterprise Active …Security , Shop
Website Hacking / Penetration Testing & Bug Bounty Hunting
Do you want to become a bug bounty hunter? Do you want to secure your website or mobile app? How about launching a new career in the world of professional penetration testing or ethical hacking? If so, this is the course for you.
This course is designed for beginners with no previous knowledge who want to learn how to test the security …
Security , Shop
Certified Information Systems Security Professional – CISSP 2021
The Certified Information Systems Security Professional (CISSP) is an information security certification for security analysts.
HOMEPAGE – https://www.anonymz.com/?https://www.itpro.tv/courses/security-skills/accelerated-cissp-2021/
Our Price: $5
Security , Shop
CISM – ITPRO.TV
The Certified Information Security Manager certification course is designed for those individuals seeking to enhance their skills, and be recognized for their expertise in Information Security Management. The course promotes the best in security practices from around the world and identifies the individual’s knowledge and expertise in this area. The course is intended for individuals seeking to demonstrate mastery of …
Security , Shop
Practical Cryptography
Practical application of modern Cryptography fundamentals. Cryptography is used EVERYWHERE security is employed. But what are the underlying tools that make Cryptography possible. This class explores those tools and should be considered a mandatory watch if you want to really understand protocols like TLS, SSL, IPsec, SSH, Password Storage, and any sort of security systems across the Internet.
HOMEPAGE – <a ...
Security , Shop
Advanced Intrusion Detection
Building meaningful detections is the first step in identifying malicious intruders on your network and remediating any threats against your environment. The Advanced Intrusion Detection learning path will provide you with the practical, hands-on knowledge you need to fully understand the methodology behind intrusion detection and craft meaningful detection rules and logic.
This learning path begins with an overview of intrusion …
Security
Showing 379–387 of 578 results